How I Write Secure Node.js Code (And You Can Too)
Learn and apply the secure coding techniques that I personally practice in my JavaScript and Node.js development day-to-day as I reveal them in these books of practical Node.js security.
- 300+ pages of Node.js secure coding analysis and vulnerability CVE review
- 120+ self-assessment questions and code quizzes
- Plenty of Node.js Secure Coding practices and insights
"All the series is an amazing work, thanks a lot for investing the time to write them"

Ulises Gascón
Express TSC & Node.js Collaborator
Bought by Developers Working at Leading Tech Companies





Master Node.js Security
Learn how to apply NodeJS Secure Coding techniques to prevent vulnerabilities in server-side JavaScript code such as Command Injection, Path Traversal, and Code Injection weaknesses that can be exploited against your Node.js applications






















 +400
+400
Join 460+ developers writing secure Node.js code
What do you get?
When you purchase these training books, here is how you level up your Node.js expertise:
- More than 300 pages of content to learn expert Node.js security
- A whooping 123 self-assessment questions to test your knowledge
- Learn secure coding techniques to prevent Command Injection vulnerabilities
- Learn hardened secure coding preventions to avoid Path Traversal vulnerabilities
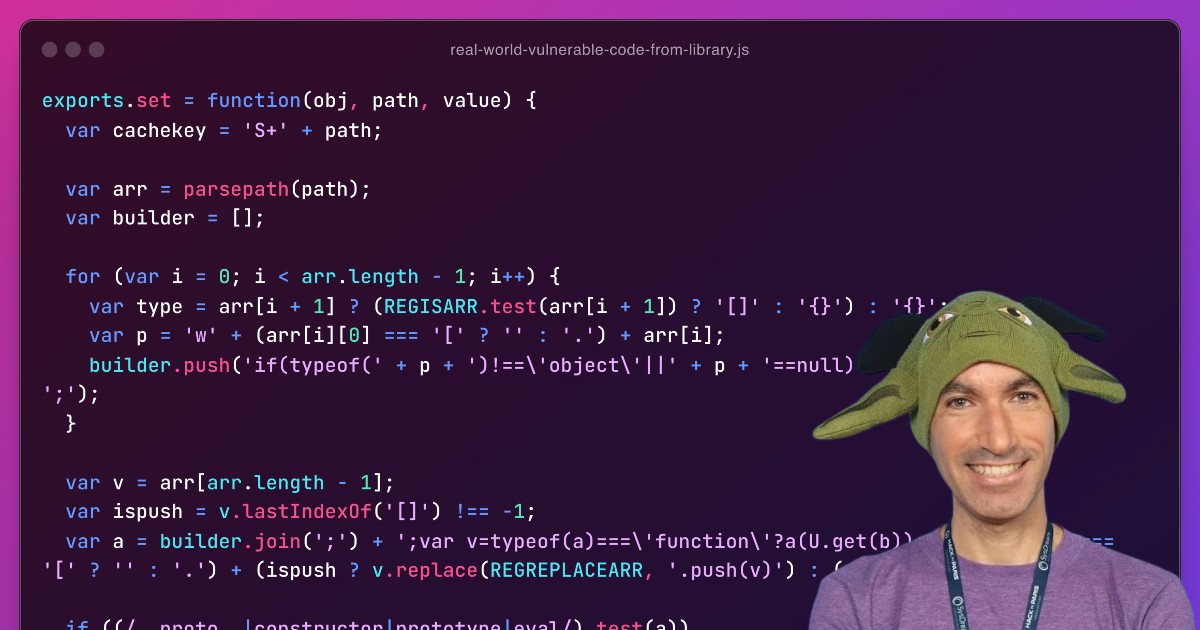
- You analyze vulnerable code found in real-world npm packages
- Learn from security mistakes of 22 vulnerable npm packages
- Cool ebook editions in Light & Dark mode
- Learn from mistakes of vulnerable packages with millions of downloads
Leading Developers Practice Node.js Secure Coding
Read testimonials by leading developers who took the training and leveled-up their skills to practice Node.js Secure Coding
"I have finished reading Node.js Secure Coding from Liran Tal. I read the whole thing in an hour without realizing it. I learned and discovered a few things along the way. I laughed at the IFS, didn't see it coming."

Thomas Gentilhomme
Node.js lead at MyUnisoft, Node Security WG
"Liran Tal, your book on Node.js security is an absolute gem! The abundance of real-world examples with commented fixes is incredibly valuable. Your practical solutions have enlightened me, especially the discovery of the shell-quote module! Recommended to all Node.js developers!"

Manuel Spigolon
Senior Software Developer at NearForm
"I wholeheartedly enjoyed working and learning from Liran's expertise in securing applications. With extensive experience speaking at global conferences and actively contributing code to the community, he is a true authority in the field. I highly endorse both his enlightening book and engaging workshop, as they are invaluable resources for anyone looking to enhance their understanding and implementation of application security"

Yoni Goldberg
Software Architect, Node.js Specialist
"Liran Tal just published a new book about Node.js secure coding. It is worth taking a look at!"

Daniel Garcia
Cybersecurity & API Security Consultant
"I highly recommend the new Node.js Secure Coding book published by Liran Tal. Covers not only Node.js but also gives you another perspective on how to achieve good and secure applications, especially with understanding and handling SAST vulnerabilities. Liran - CHAPEAU!"

Eli (Tom) Lelonek
Application Security Manager at Allot
"Got my copy of Node.js secure coding! I already know I'll learn a lot 🔥"

Marco Ippolito
Node.js Collaborator & Developer Experience Engineer @NearForm
"A very interesting book that I recommend if you are in the Node.js world is "Node.js Secure Coding" by Liran Tal. Laid out with explanations, examples and tips. Warmly recommended."

Diego Betto
Founder & Senior Fullstack Developer
"Read trough first 3 chapters last night, nice work Liran!"

Aranđel Šarenac
12+ years developer, focusing on Identity Security
"Highly recommend Liran Tal's ebooks for any Node developers who are serious about security (which should be all of you!)"

Alicia Sykes
Principal Engineer @AND Digital
"Started reading the Prevention and Exploitation of Path Traversal and I am very happy with the quality. It is connecting me to some knowledge I had from working in AV company and now with code, very interesting."

Yana Ifraimov
NOC Engineer @Skai
"Node.js security rock-star Liran Tal drops another book on how to ship safe Node.js applications. I know it's hard to tell sometimes where to start from when it comes to security, as the internet is flooded with content. Well, look no more - trust content composed by Liran"

Gal Weizman
Browser JS Application Security at MetaMask & LavaMoat
"It's not every day that you can pay less than $20 for years of security wisdom. Just got this and will be using the book during my streams to improve my code."

Ray Fernando
AI app at TruthTorch.ai, ex-Apple Engineer
"The amount of content covering advanced topics in Node.js is so little, makes this a must-read"

Ruan Martinelli
Product engineer, Full-stack Freelancer & Consultant
"Outstanding book, can't wait."

Tiger Abrodi
TypeScript fanatic
"I've followed Liran Tal's work for years and definitely one of the top experts in Node.js security! Give these a look as they are essential for anyone serious about securing their Node.js applications."

Zac Rosenbauer
CTO & Co-founder at Joggr
"If you're a developer looking to better understand security vulnerabilities, this is one of the best books out there on the topic. While this book specifically focuses on Command Injection vulnerabilities in Node, the content contained within is broadly applicable to any developers writing software. It's an A++ book and absolutely worth the time to read and analyze. Liran is a top-tier security researcher and developer who's an icon in the security space. Seriously, look him up on Google, he's amazing."

Randall Degges
Head of Developer Relations & Community at Snyk
"Psyched to get my copy of Liran Tal's book: "Node.js Secure Coding: Defending Against Command Injection Vulnerabilities" Do yourself a favor and grab a copy!"

Micah Silverman
Director, DevSecOps Acceleration at Snyk
"I am just starting to read it now that I am doing security patching in Express. The book looks amazing! I mean... all the series is an amazing work, thanks a lot for investing the time to write them."

Ulises Gascón
Express TSC & Node.js Collaborator
"On point content, short book just for my liking. I like the interesting facts in the middle and code examples are good. I like the approach of Risk -> Solution -> Implementation"

Sumit Kumar
Full-Stack Engineer at Optmyzr
"This was targeted at a perfect level for me, as someone who had exposure to these topics, had done some fiddling with helmet previously in node, but this was a great succinct guide to quickly and effectively teach "what" and "why"."

Luke Rasmussen
Software Engineer
Security Analyst for the Node.js Foundation
In his role as a security analyst in the Node.js Foundation's Security Working Group, Liran reviewed hundreds of vulnerability reports for npm packages and established processes for responsible security disclosures and vulnerability triage 🏴☠️.
Education is a core practice
Passionate about educating developers on application security and secure coding practices, Liran is a world-wide international speaker, workshop instructor, and author of several books on the subject. He occasionally speaks on software security topics at academic institutions, such as presenting to students at the Electrical and Computer Engineering School at Purdue University 🎓.
Award-winning GitHub Star ⭐️
Liran received the GitHub Star recognition award from GitHub for his work educating and inspiring developers and actively advocating for web security.
Recipient of the Pathfinder for Security Award 🎖️
Honored by the OpenJS Foundation with the Pathfinder for Security Award, Liran is recognized for his work advancing Node.js security.
I'm a Security Researcher
An accomplished security researcher, Liran has disclosed security vulnerabilities in various open source software projects, including being credited with CVEs to his name for vulnerabilities in npm packages with millions of downloads.
Acclaimed Recognition at Black Hat
Liran's discovery in supply chain security research, including Lockfile Injection, was presented at the prestigious Black Hat Europe 2021 cybersecurity conference. Liran is also the creator of several developer security tooling projects such as npq, is-website-vulnerable, and snync, which help developers and enterprises defend against dependency confusion attacks.
About Liran Tal
Liran Tal is an accomplished software developer, respected security researcher, and prominent advocate for open source software in the JavaScript community. As an experienced author and educator, Liran has written several widely respected books on software security. These include "Serverless Security" published by O'Reilly, as well as the self-published titles "Essential Node.js Security" and "Web Security: Learning HTTP Security Headers". Liran's leadership in open source security includes significant contributions to OWASP projects, recording supply chain security incidents at the CNCF, and various OpenSSF initiatives. Currently, Liran is a developer advocate at Snyk where he empowers developers with the knowledge and tools needed to build and deploy secure software.
Sharpen your Node.js Coding Skills
Here is a classic Fastify application code. Can you find the security vulnerability in the code below?
Vulnerable Code
Toggle Hint import fs from "node:fs"
import path from "node:path"
import fastify from "fastify"
fastify.get("/static", async (req, rep) => {
const filename = req.query.filename
const filePath = path.join(
"/opt/app/uploads", filename)
const fileContents = fs.readFileSync(filePath)
rep.code(200).send(fileContents)
});
fastify.listen({ port: 3000 })Don't give in to security vulnerabilities.
$ npm install url-parse serve @sveltejs/kit next react-svg added 74 packages, and audited 74 packages in 24s 24 high severity vulnerabilities Master Node.js security and secure coding best practices through analyzing and exploiting real-world vulnerable npm packages.
Bought by Developers From These Companies
















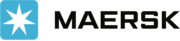












Digital book
PDF & EPUBThe book features:
- 106 Pages
- 12 Vulnerable npm Packages
- 33 Self-assessment Questions
- 10 Chapters
- Light Mode
- Dark Mode SPECIAL EDITION
- July 2023 release
- Sale 15% OFF
Tip:
get 2 secure coding books bundle for $120.96 and save 30%
Buy Bundle
Admired by application security professionals
Loved, recommended, and praised by security professionals heroes worldwide. Here's what they have to say:
"If you're a Node.js developer you need this book! Always been a huge fan of your work! You earned the praise many times over Liran"

"Covers not only Node.js but also gives you another perspective on how to achieve good and secure applications, especially with understanding and handling SAST vulnerabilities."

"As opposed to other online resources, Liran really pins down the dangers with untrusted code and the complexity with confining it in the realms of JavaScript - a great cover for such an important security topic!"



Digital book
PDF & EPUBThe book features:
- 117 Pages
- 7 Vulnerable npm Packages
- 40 Self-assessment Questions
- 11 Chapters
- Light Mode
- Dark Mode SPECIAL EDITION
- September 2023 release
- Sale 15% OFF
Tip:
get 2 secure coding books bundle for $120.96 and save 30%
Buy Bundle
Test your Node.js Secure Coding skills
Is the code below vulnerable to a Path Traversal attack?
Vulnerable code... is it?
const fastify = require('fastify')
const path = require('path')
const downloadsPath = '/opt/downloads'
const app = fastify()
app.get('/download', async (req, rep) => {
const file = req.query.file || 'default.png'
if (file.includes('..')) {
return rep.code(400)
.send('Directory Traversal Detected')
}
const normalizedFilename = path.normalize(file)
const downloadFilepath = path.resolve(
downloadsPath,
'downloads',
normalizedFilename)
try {
await rep.sendFile(downloadFilepath)
} catch (err) {
rep.code(404).
send('Requested File Not Found')
}
})
Literally, the only Node.js Secure Coding books on Amazon.
Get the paperback version of Node.js Secure Coding books on Amazon.com.
Even better, SAVE 30% and get 2 digital editions of Node.js Secure Coding books in PDF and EPUB straight to your inbox.
Get 2 Books for $120.96Defend Against Command Injection in Node.js
Security Education Modules in the Book
Introduction to Application Security
Master application security essentials—CVEs, CWEs, OWASP Top 10. Elevate your Node.js skills, fortify defenses, and navigate the security landscape.
Command Injection
Explore command injection vulnerabilities' landscape, types, and real-world impact. Classify vulnerabilities, detect insecure code patterns, and fortify applications
Mitigating Argument Injection in Node.js Applications
Secure Node.js Apps: Lessons from Command Injection Vulnerabilities. Learn key strategies to avoid OS injection risks, optimize code, and safeguard against argument injection attacks
Fortifying Node.js Applications Against Command Injection Threats
Mastering Node.js Security: Advanced Defense Against Command Injection. Learn crucial tactics beyond basics—robust input validation, nuanced security controls, and insights from real-world vulnerabilities. Elevate your Node.js applications' security posture.
Hardening Node.js Against Command Injection: Insights from vulnerable npm package
Securing Node.js Projects: Unraveling Git-Promise Vulnerability. Delve into input validation nuances, persistence of vulnerabilities post-fix, and project popularity impact. Equip yourself with insights to fortify Node.js projects against evolving security landscapes
Navigating Command Injection Pitfalls in vulnerable npm package: A Technical Deep Dive
Mastering Secure Integration: Lessons from ImageMagick Vulnerability. Explore pitfalls of exec() API, balance convenience with security, and adopt secure alternatives. Navigate Node.js security with confidence
Defending Against Command Injection: Lessons from a Strapi vulnerability
Securing Strapi: Navigating Command Injection Risks. Uncover vital insights from a CVE vulnerability, emphasizing input sanitization, secure APIs, and cautious handling of user input. A practical guide for fortifying applications against command injection threats
CLI Security: Leveraging GitHub as an attack vehicle against vulnerable CLIs
Command-Line Insecurity: Demystifying CLI Vulnerabilities. Delve into the 2018 discovery, debunking myths around CLI security. Uncover GitHub as an attack vector, highlighting the deceptive nature of data sources. Developers gain insights into robust input validation for fortified application security
Mastering Secure Command Execution in Node.js
Node.js Command Injection Defense: Mastering child_process APIs and Secure Coding. Navigate secure execution with insights on API choices, escaping strategies, and npm run-scripts. Equip yourself to proactively prevent vulnerabilities for robust Node.js application security
Deepening Your Command Injection Defenses
Mastering Command Injection Defenses: Test Your Knowledge, Real-world Examples, and CVE References. Elevate your understanding with quizzes, real-world insights, and a comprehensive CVE reference list. Equip yourself to fortify command injection defenses and communicate security priorities effectively
Prevent Path Traversal in Node.js
Security Education Modules in the Book
Security Foundations for Node.js Development
An introductory chapter unfolds core security concepts and terminology for developers. Master CVE, CWE, OWASP Top 10, and other security-lingo terms in modern software development.
Navigating Path Traversal Hazards in Node.js Applications
Journey through path traversal intricacies. Mitigate risks in Node.js apps. Secure coding guide for JavaScript developers building server-side applications .
Decoding Path Join: Navigating Security Pitfalls in Node.js
Decode path traversal nuances. Expose insecure coding practices. Learn vulnerable code patterns and embrace insights for robust, secure Node.js coding.
Unveiling Nuances: Beyond the ../ String in Node.js Path Traversal
Explore path and directory traversal subtleties. Decode percent-encoding pitfalls. Adopt high-precision secure coding best practices when dealing with core Node.js filesystem APIs for optimal Node.js security.
Mastering Security: Navigating Nuances Beyond Classic Path Traversal in Node.js
Unearth secure coding lessons. Explore adjacent paths and logic checks. A beacon for Node.js developers that seek security controls and writing production-grade code.
Unveiling Vulnerabilities: The Anatomy of Simple Code's Impact on Security
Dissect quickly written code implementations that result in secure coding errors and learn to avoid core Node.js API pitfalls.
Navigating the Maze: Path Traversal Vulnerabilities in HTTP server npm devtools
Analyze directory traversal bugs. GitHub repository insights and lessons from oversights in CLI configuration that go from logic error to security vulnerabilities risking development environments.
A Deep Dive into Security Oversights in a File Server npm devtool
Explore npm package devtools that introduce security risks for developers. Insights into secure coding intricacies unfolding in CLIs that do not implement security controls.
Path Traversal Beyond Deny-lists and Operating System Support
Wake up call on deny-lists. Cross-platform compatibility insights. Layers for comprehensive security and understand how overlooked bad practices end up a security implication.
Offensive Security: Automation, Exploitation, and Node.js Vigilance
Employ tactical offensive security tools to learn how hackers automate path traversal exploits. In this chapter we highlight Node.js runtime vulnerabilities and required vigilance for your production apps.
Mastering the Craft: Secure Coding Strategies to Prevent Path Traversal in Node.js
Meticulous guide for secure coding, demonstrating hands-on and best practices advice for Node.js developers. Adopt symbiotic coding and testing for robust defenses.
Master Node.js Security Through Hands-On Learning and Best Practices
Comprehensive learning path
Whether you're a beginner or an experienced JavaScript developer, this Node.js Secure Coding book takes a comprehensive approach to security. From basic terminology to introduction to Command Injection, you'll learn about assorted patterns of insecure code observed in popular and well-known npm packages.
Hands-on learning
Unlike other security books that rely on theoretical examples, this book is based on real-world vulnerable code found in popular npm packages. You'll get hands-on experience reviewing and fixing security issues in these projects, learning practical security skills and Node.js secure coding best practices.
Best practices and practical takeaways
Each chapter ends with a summary of the lessons learned, highlighting best practices for securing your Node.js code and improving your overall security knowledge of Command Injection vulnerabilities.
Congratulations!
You've leveled up your security skills!
Liran is a tireless advocate for security in the JS ecosystem. He works hard to build bridges, educate developers about security issues, and support Open Source projects working to improve their security posture. Liran has served on the Node security team and is always available to support developers!
by the OpenJS Foundation
Hands-On
Node.js Security
Master secure coding in Node.js with real-world vulnerable npm dependencies and experience secure coding and offensive security hacking first-hand

Node.js Secure Coding: Defending Against Command Injection Vulnerabilities


