
How to use npm audit
Getting started with the npm audit command and learn why it's not enough and how to advance your project's security posture with more robust security tools like Snyk.

Getting started with the npm audit command and learn why it's not enough and how to advance your project's security posture with more robust security tools like Snyk.
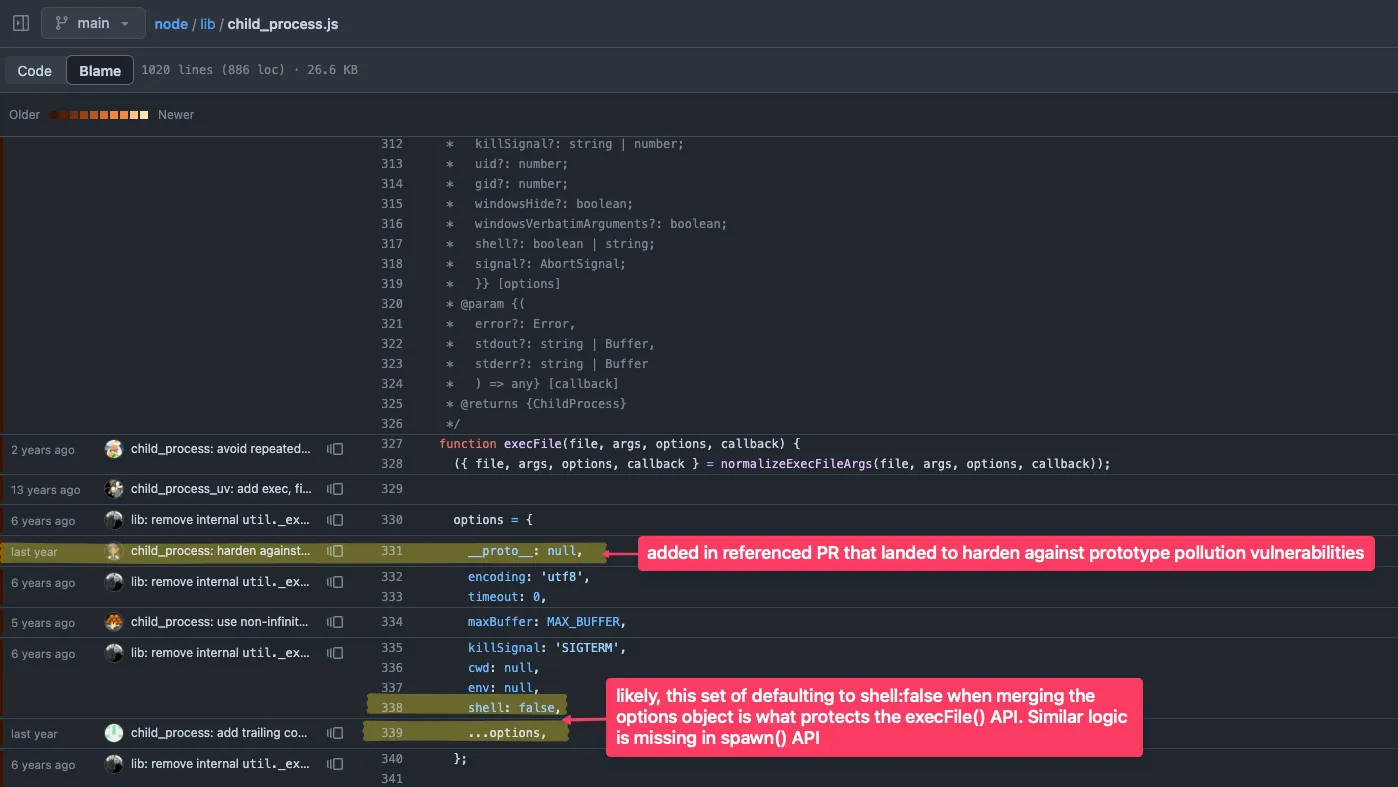
Learn how I discovered a Node.js core prototype pollution regression, its security implications, and why it didn't warrant a CVE. Luckily, I also fixed it for us!

JavaScript developers need security skills to safeguard user data, prevent application breaches, and maintain user trust. Learn about essential security skills for writing secure code and fixing vulnerabilities in JavaScript applications.

The most upvoted Reddit answer to a question about serving images via a route in Express.js is a security vulnerability waiting to happen.

Enhance your development workflow with JavaScript security best practices. Learn about Content Security Policy (CSP) in Nuxt.js, avoiding `eval` and `new Function` with untrusted input, secure DOM manipulation, cookie security, and third-party integration.

Can you spot an Insecure Direct Object Reference (IDOR) vulnerability in your JavaScript application? Learn what IDOR is, how it can be exploited, and how to prevent it in your code.