~ 5 min read
10 Best Practices for Secure Code Review of Node.js code

In a prior article we learned why secure code review is important to Node.js. In this article we want to explore paramount code review skills that is paramount to Node.js and JavaScript developers in ensuring code quality and security.
Let’s get started with my recommendations for secure code review practices that are ideal and will help enhance your code review process to foster a culture of secure coding.
1. Node.js API Documentation
Consult the official Node.js API documentation regularly. Familiarity with the documentation ensures you’re using Node.js APIs correctly and securely. Leverage the documentation’s code examples to understand how to implement features securely.
One example where this is paramount is when you work with cryptographic operations. The Node.js crypto module provides cryptographic functionality that includes a set of wrappers for OpenSSL’s hash, HMAC, cipher, decipher, sign, and verify functions.
Reading the Node.js API carefully to understand how to leverage the crypto module to implement cryptographic operations securely is key to avoid security issues.
2. Utilize Secure APIs
Always opt for secure versions of Node.js APIs when available. For instance, prefer the crypto module for cryptographic operations rather than attempting custom implementations.
One example where this is paramount is the Node.js exec function which is used to execute commands in a shell and buffer the output. The exec function is a common source of command injection vulnerabilities in Node.js applications.
3. Dependency Scanning
Integrate dependency scanning tools like Snyk or the Snyk Advisor into your code review process where it is relevant to review newly added or updated dependencies.
Regularly check for known vulnerabilities in your project’s dependencies and address them promptly.
4. Code Security Linting
Enforce code linting rules specific to Node.js and JavaScript using tools like ESLint. Customize ESLint rules to include security-focused guidelines, ensuring your codebase adheres to best practices.
If you choose ESLint, then you have the eslint-plugin-security plugin which provides ESLint rules for Node.js security.
However, ESLint and the eslint-plugin-security is very rigid and doesn’t provide much flexibility. You may end up with a lot of false positives and it’s not very easy to customize the rules.
I’m biased but I’d recommend you take a look at Snyk Code which provides you with secure code linting in real-time on your VS Code IDE. It’s free too.
👋 Just a quick break
I'm Liran Tal and I'm the author of the newest series of expert Node.js Secure Coding books. Check it out and level up your JavaScript
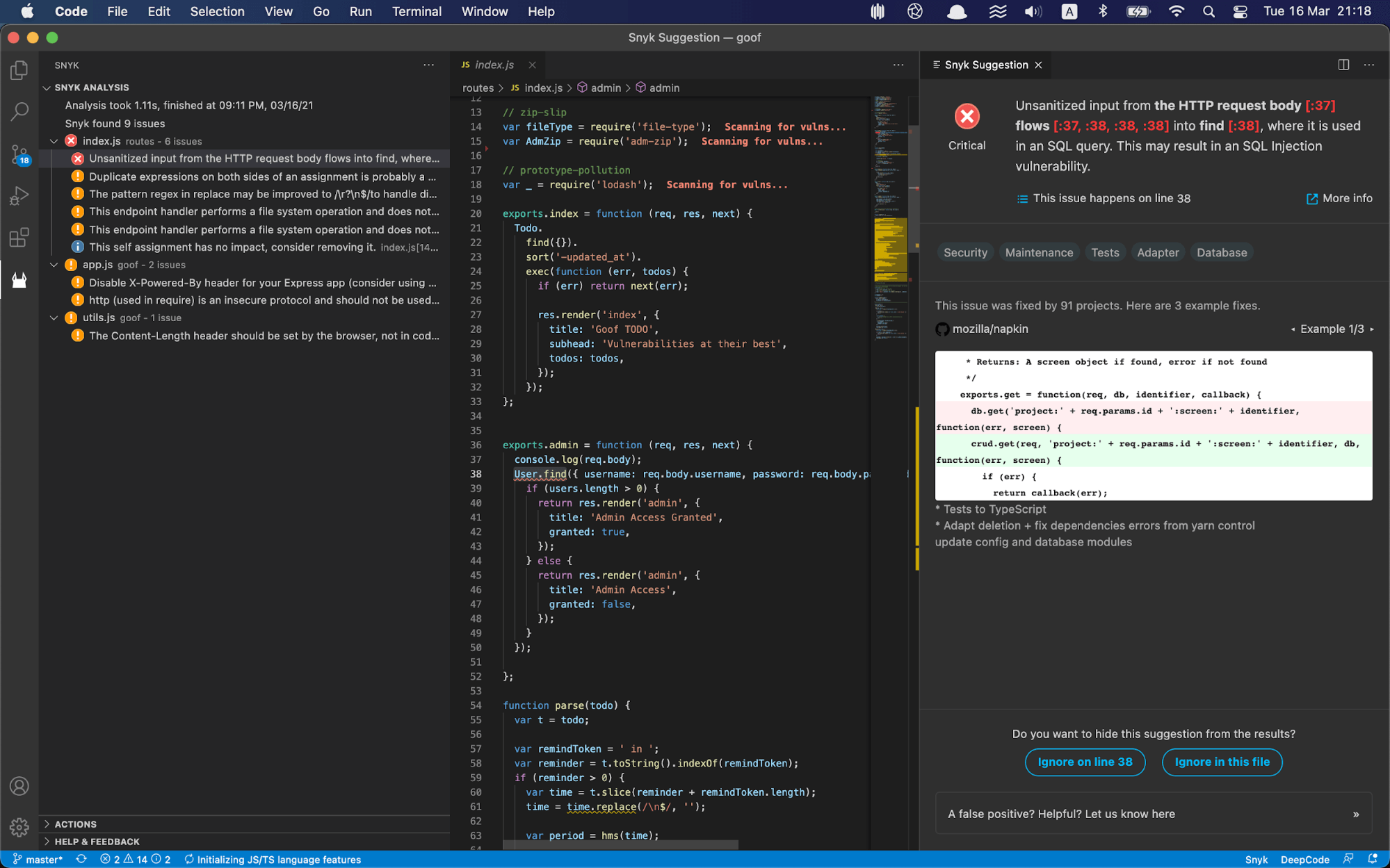
5. Data Validation and Sanitization
Emphasize the importance of input validation and data sanitization in code reviews. Ensure that user inputs are properly validated and sanitized to prevent common vulnerabilities like SQL injection or command injection. Encourage the use of established libraries for input validation and sanitization, such as the validator library for JavaScript.
6. Staying up to date with Node.js releases
Stay updated with the Node.js release notes to identify security enhancements and new features.
7. Error Handling
Review error handling practices to prevent information leakage. Avoid exposing detailed error messages to users. Encourage the use of custom error handling middleware to centralize error management and enhance security.
Another important tip here is to take notice you don’t leak data from process.env as that is a very common source of information leakage.
8. Secure Package Management
Educate developers about secure package management practices. Ensure they only install trusted packages from reliable sources.
Implement lockfile linters such as lockfile-lint to ensure that dependencies specified in the lockfile adhere to pre-defined security policies and mitigate a vector of attack where malicious actors can tamper with the lockfile.
9. Threat Modeling
Introduce threat modeling during code review discussions. Encourage developers to identify potential security threats and vulnerabilities in their code.
Consider using threat modeling tools or frameworks tailored for Node.js security assessments.
10. Continuous Education
Emphasize continuous education within your development team. Encourage developers to stay updated on security best practices through training, workshops, and online resources.
Promote participation in Node.js and JavaScript security communities to learn from peers and experts.
Two resources I’d recommend you check out are:
- The Snyk Learn educational platform which is open and free for everyone to learn about security.
- My book Node.js Secure Coding: Defending Against Command Injection Vulnerabilities which is a practical guide to understanding, identifying, and mitigating command injection vulnerabilities in Node.js applications.
What’s next? Skill up with Node.js Secure Coding
We covered a blend of intricacies relating to conducting effective code reviews in the world of Node.js and JavaScript development. By integrating these Node.js and JavaScript-specific best practices into your secure code review process, you’ll empower your team to develop secure and resilient applications.
As a next step, I invite you to explore: Node.js Secure Coding: Defending Against Command Injection Vulnerabilities 🌟
This Node.js security book is a comprehensive resource designed to deepen your understanding of command injection vulnerabilities and equip you with the skills needed to defend against them effectively. Dive into real-world vulnerable npm package code examples, practical self-assessment Node.js security questions, and expert insights to bolster your Node.js security expertise.
Visit https://www.nodejs-security.com to learn more and take your Node.js development to a new level of security. Secure coding isn’t just a goal; it’s a journey, and I’m here to guide you every step of the way.

