~ 3 min read
North Korea malware on npm and Ledger connect-kit crypto heist

North Korea threats on npm software supply chain with malicious packages
North Korean state-sponsored threat actors have been carrying out increasingly sophisticated supply chain attacks aimed at infiltrating target organizations. By compromising popular open source packages and repositories, they undermine the inherent trust within the developer community to distribute malware.
Recent investigations uncovered an attack affecting the npm package registry, which exploited the preinstall script in package.json files to fetch and execute a remote payload. Further analysis linked this activity to the notorious North Korean Lazarus cybercrime group. The attack indicates North Korea’s persisting efforts to evolve its cyber warfare capabilities by targeting software supply chains.
This supply chain attack leveraged various techniques including open source package poisoning through trusted repositories like GitHub and direct exploitation of package managers like npm. After gaining an initial foothold, the threat actors employed multi-stage malicious scripts and processes to eventually fetch and activate remote payloads, covering their tracks.
JavaScript CDN leveraged for crypto heist due in Ledger connect-kit library
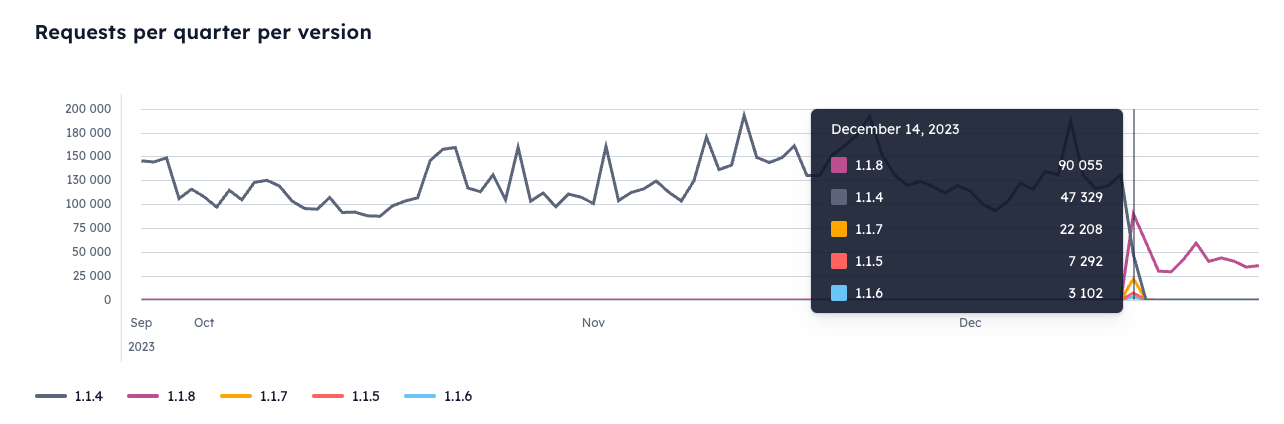
On December 14th, the crypto world narrowly avoided disaster when the widely used Ledger Connect Kit JavaScript library was compromised in a supply chain attack. Some slick social engineering, spear-phishing and bad employee off-boarding IT practices gave hackers access to publish malicious versions 1.1.5 to 1.1.7 on npm for the connect-kit package. These versions contained nasty code that redirected wallet connections to hacker accounts using a fake WalletConnect module.
During the roughly 5 hours the corrupted code was live, around $600k was stolen before Ledger’s security squad rolled out version 1.1.8 to plug the hole. So while the attack stung, it could have been far more damaging.
The Ledger connect-kit incident is what happens when you don’t have internal security practices: threat modeling, secure code review and security champions are some that would have helped prevent this dire web3 malware.
This scary incident puts software supply chain risks into stark focus. As JavaScript developers, many of us tool around on npm without thinking twice about the integrity of those dependencies we inject into our apps. But the truth is, we’re often working on a foundation of trust in people we’ve never met before.
Even within the short-time frame in which the malicious versions of Ledger’s connect-kit package were alive, the malicious code was downloaded over 30,000 times from browsers who served the JavaScript library from the CDN.
So we’d all be wise to take heed – reinforce your package validation checks, pin to specific dependency versions, monitor alerts about new vulnerabilities, and keep audits on your third-party code usage. Most importantly, don’t serve latest versions of JavaScript scripts over a CDN. Stay vigilant out there folks, or you could be next!