~ 3 min read
A Node.js Vulnerability Scanner to Avoid Security Risks of EOL Runtime Versions

Running Node.js in production environments? Security should be your top priority. Thankfully, the community has tools like is-my-node-vulnerable which is a sort of Node.js vulnerability scanner, created by Node.js TSC member Rafael Gonzaga to help you stay ahead of potential threats.
What is is-my-node-vulnerable?
This lightweight CLI tool can be a lifesaver for Node.js developers. It scans your system and compares your installed Node.js version against a comprehensive database of known vulnerabilities (a CVE database), alerting you to potential risks in-case you are running a Node.js runtime version which is unpatched.
Imagine finding out your runtime is susceptible to vulnerabilities like CVE-2023-32002 (Remote Code Execution) or CVE-2023-32004 (Prototype Pollution) before attackers do. Using a tool like is-my-node-vulnerable helps you address these issues promptly, keeping your running Node.js in shape.
Using is-my-node-vulnerable as a Node.js vulnerability scanner
Install it globally using npm: npm install -g is-my-node-vulnerable. Other use methods includes the programmatic API which the library exposes so you can put it in your production code-base and fire events when the Node.js application bootstraps, then track those in your dashboards and events system.
If you installed the CLI, scan your system by simply running is-my-node-vulnerable in your terminal and you’ll get alerted: The tool displays clear results with a cool ASCII art print-out (nice work Rafael!), indicating if your Node.js version is vulnerable and providing details about the identified risks.
$ node -v
v15.14.0
$ npx is-my-node-vulnerable
██████ █████ ███ ██ ██████ ███████ ██████
██ ██ ██ ██ ████ ██ ██ ██ ██ ██
██ ██ ███████ ██ ██ ██ ██ ███ █████ ██████
██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██ ██
██████ ██ ██ ██ ████ ██████ ███████ ██ ██
v15.14.0 is end-of-life. There are high chances of being vulnerable. Please upgrade it.Critical path traversal and why you need a Node.js vulnerability scanner
If you don’t already understand the importance of staying up to date with patched Node.js runtime versions then let’s explore with a bit more details, such as the case in time in which Node.js was vulnerable to a path traversal.
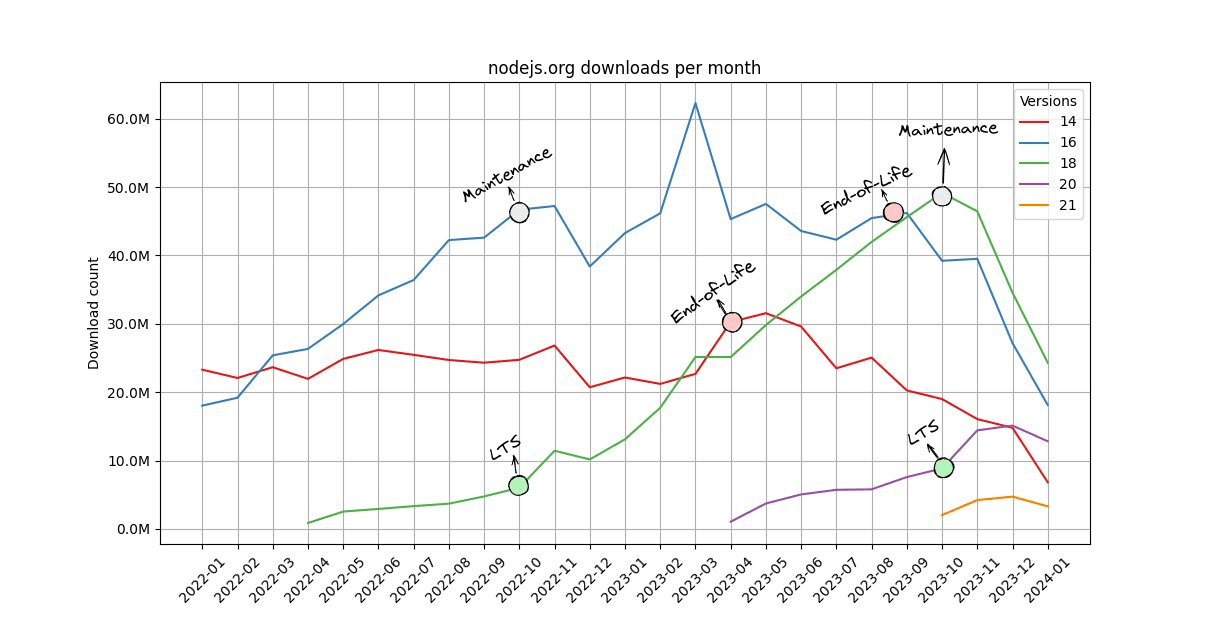
Staying vigilant for vulnerable Node.js versions requires ongoing attention and continuous vulnerability scanning. The graph shared by Rafael highlights a worrying trend: Node.js 14, declared End-of-Life (EOL) in April 2023, still saw 30 million downloads the following month. Running EOL versions significantly increases your risk, as they no longer receive security patches. Remember, a single vulnerability in your runtime can be a gateway for attackers.
Case in point: Node.js 8.5.0, declared EOL in December 2019, was susceptible to a critical Path Traversal vulnerability (CVE-2019-11358). This vulnerability could be easily exploited using automated offensive security tools, potentially granting attackers access to sensitive data or even system control.
Don’t wait for disaster to strike. Integrate is-my-node-vulnerable into your development workflow for regular vulnerability checks. Make sure to upgrade to supported Node.js versions as soon as new releases become available, and use tools like Snyk to scan your open-source dependencies and your Node.js runtime version in Docker containers.
But, you can do even better! 👇
For a deeper dive into Path Traversal vulnerabilities and how to protect your Node.js applications, get my book Node.js Secure Coding: Prevention and Exploitation of Path Traversal Vulnerabilities